- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-09-21
ITSEC Newsletter 2023-09-21
Red team is best team
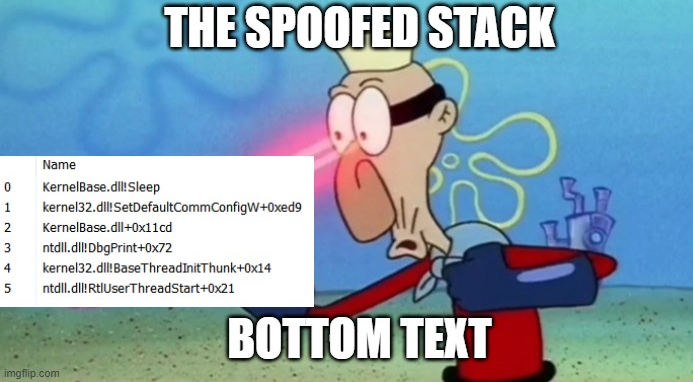
"Stack spoofing is a really cool malware technique that isn’t new, but has been receiving some more attention recently. The goal of this post is to introduce readers to the concept and dive into two implementations. This post will focus only on call stack spoofing in x64 Windows with “active” spoofing techniques."
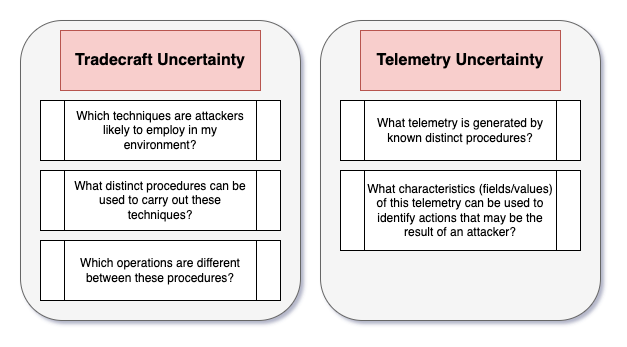
"This post is the first in what will likely be a series that traces reaction correspondences for well-known attack techniques. The overall goal is to explore the ways in which attackers and defenders can combat uncertainty in both tradecraft and telemetry. This post focused exclusively on tradecraft uncertainty, but future posts will explore how Cartographer’s data model can be used to combat telemetry uncertainty as well."
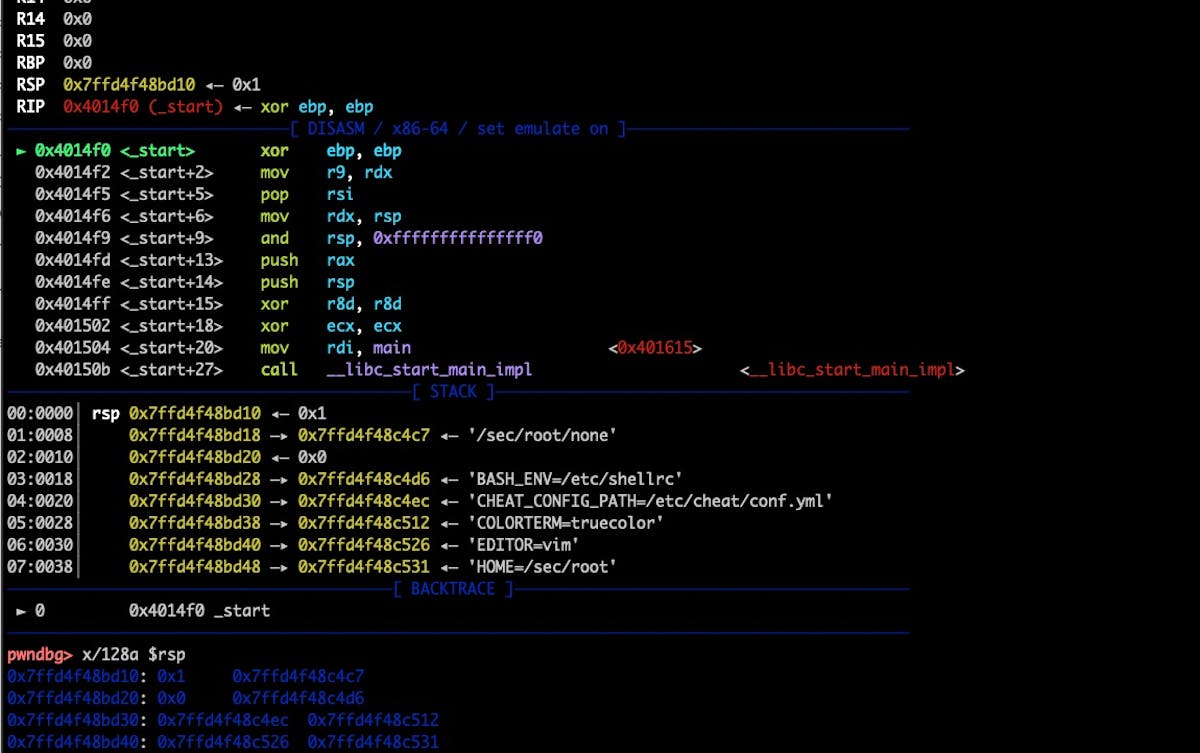
"In this article, you will learn what happens inside the Linux Kernel when a process calls execve(), how the Kernel prepares the stack and how control is then passed to the userland process for execution. I had to learn this for the development of Zapper - a Linux tool to delete all command line options from any process (without needing root)."