- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-09-14
ITSEC Newsletter 2023-09-14
Red team is best team
"A few months ago I wrote about two vulnerabilities I found in the TPM 2.0 reference implementation code. While trying to verify if the virtual TPM of Microsoft's Hyper-V was affected, I found that this virtual component runs as an Isolated User Mode (IUM) process, which means that it's not possible to attach a debugger to it, not even having elevated privileges. After looking for information on how to debug this kind of processes, I found slices of data scattered around the Internet, but no clear instructions about how to do it. After putting all the pieces together, I decided to write this in the hope that someone else doing research will find it useful."
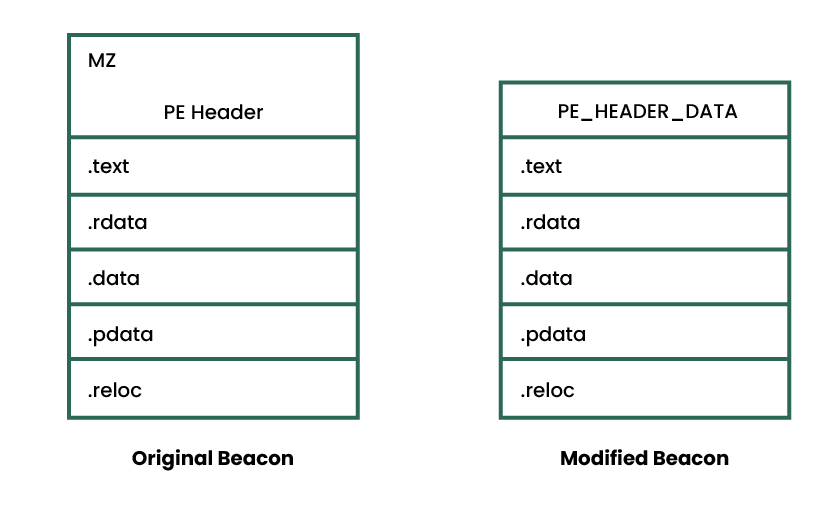
"In this instalment, we’ll build upon the original UDRL-VS loader and explore how to apply our own custom obfuscation and masking to Beacons with UDRLs. The primary intention of this post is to demonstrate the huge amount of flexibility that is available to UDRL developers in Cobalt Strike and provide code examples for users to apply to internal projects. To accompany this post, we’ve added an “obfuscation-loader” to the UDRL-VS kit and made some changes to the solution itself. UDRL-VS started out as a simple example loader that you could debug in Visual Studio. It is now a library of loader functions that will grow over time. At present, we have a “default-loader” (the original UDRL-VS loader) and an “obfuscation-loader” (the example described in this post). The move to a library simplifies the maintenance of the kit but should also improve the user experience when developing custom loaders."
"Windows arbitrary file deletion vulnerabilities should no longer be considered mere annoyances or tools for Denial-of-Service (DoS) attacks. Over the past couple of years, these vulnerabilities have matured into potent threats capable of unearthing a portal to full system compromise. This transformation is exemplified in CVE-2023-27470 (an arbitrary file deletion vulnerability in N-Able’s Take Control Agent with a CVSS Base Score of 8.8) demonstrating that what might initially seem innocuous can, in fact, expose unexpected weaknesses within your system. As a follow up to the Escalating Privileges via Third-Party Windows Installers blog post, this post will delve further into the realm of file-based local privilege escalation attacks. We will unravel and showcase how Time-of-Check to Time-of-Use (TOCTOU) race condition vulnerabilities could enable attackers to delete files on a Windows system and demonstrate how they can subsequently be leveraged to secure an elevated Command Prompt. Furthermore, we will equip software developers with the knowledge to counteract these potential threats."