- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-07-27
ITSEC Newsletter 2023-07-27
Red team is best team
"The offensive security industry is a curious one. On the one hand, we are ahead in various trends (or “thought leadership,” as some would have us term it) and are used to literally “moving fast and breaking things.” On the other hand, we’re far behind similar disciplines. One major area where offensive security has historically been a bit lacking is proper software engineering for offensive tooling. From proper unit testing to continuous integration/continuous delivery (CI/CD) integration, we’re sometimes behind our more mature industry parallels."
"Active Directory Certificate Services (ADCS) is a Microsoft feature and server role that allows organizations to establish an on-premises Public Key Infrastructure (PKI). Threat actors have been actively documented abusing misconfigurations in ADCS to escalate privileges within a Windows domain. In June 2021, eight privilege escalation primitives - ESC1 to ESC8 - were documented by SpectreOps in a whitepaper titled "Certified Pre-Owned: Abusing Active Directory Certificate Services". This blog post will dive into the most common vulnerabilities encountered by Lares engineers namely ESC1, ESC3, ESC4, and ESC6."
"If you remove the first word from the string "hello world", what should the result be? This is the story of how we discovered that the answer could be your root password!"
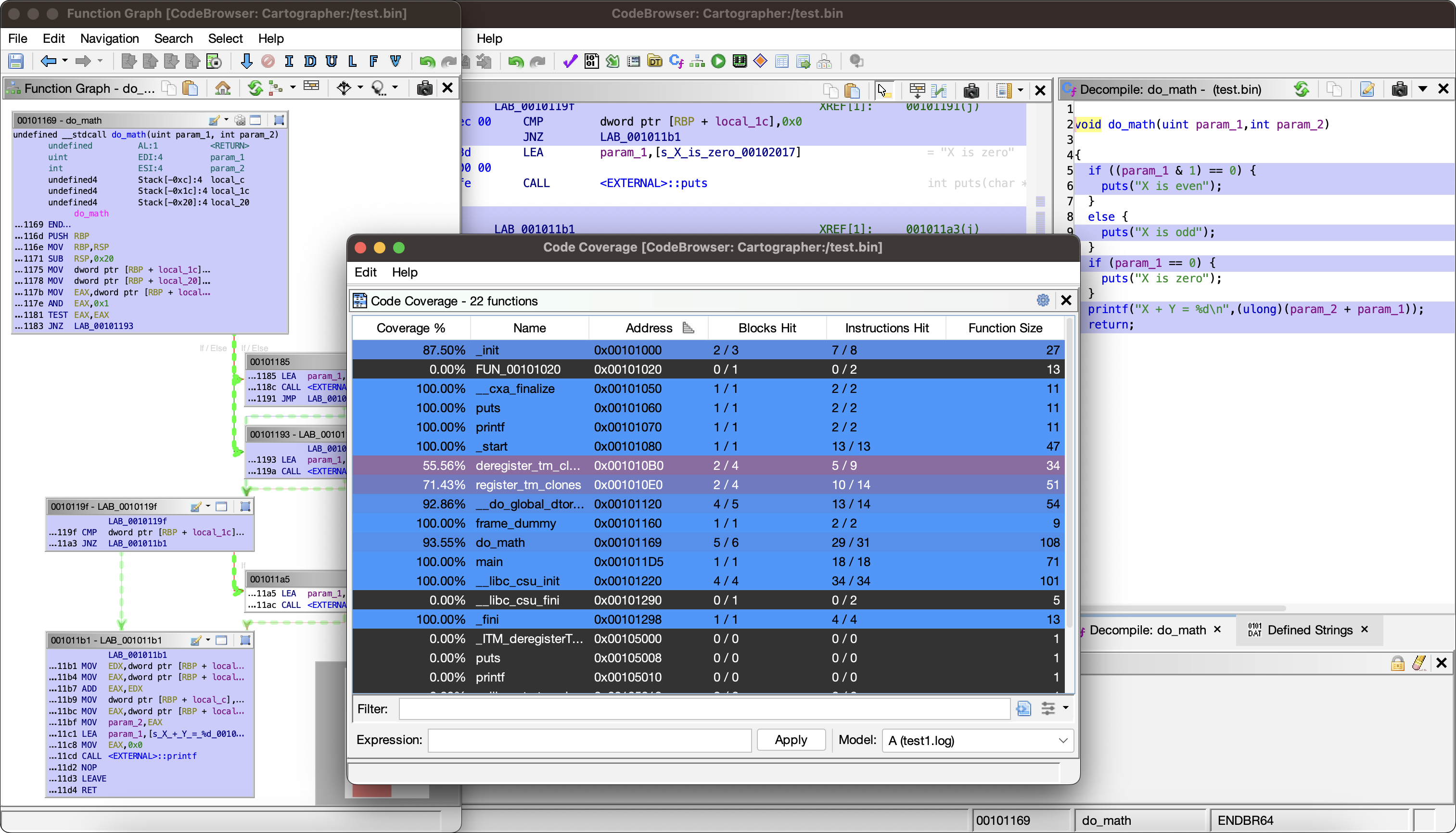
"Back in 2017, there was a new and incredibly useful plugin for IDA Pro called Lighthouse, which not only colorized code coverage data, but it also provided many useful tools for researchers, such as displaying function heat maps and the ability to perform logical operations on multiple loaded coverages. When Ghidra was released back in 2019, many researchers (myself included) eagerly awaited a version of Lighthouse for Ghidra. When 2022 rolled around and there was still no sign of a Ghidra version of Lighthouse, I decided to make my own."
"Incident Response and forensic analysts use the contents of prefetch files in investigations to gather information, such as the source from which an executable was launched, how many times it was executed, what files it touched, and the date and time it was launched. A prefetch file is like the little brother that tells the parents who broke the lamp."