- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-06-29
ITSEC Newsletter 2023-06-29
Red team is best team
"In practice, however, not all oracles are created equal: an oracle that comes from error messages may well be perfectly reliable, whereas one which relies on (say) timing side channels may have to deal with a non-negligible amount of noise. In this post, we’ll look at how to deal with noisy oracles, and how to mount attacks using them. The specific cases considered will be MAC validation and PKCS7 padding validation, two common cases where non-constant-time code can lead to dramatic attacks. However, the techniques discussed can be adapted to other contexts as well."
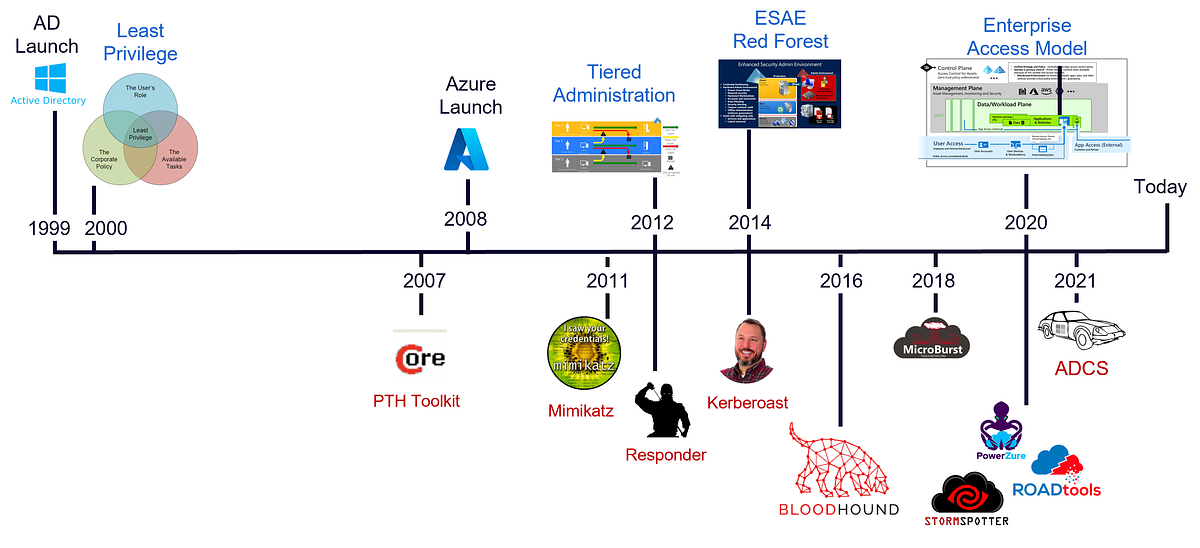
"We want to make this process of determining Tier Zero easier for organizations. In this blog post series, we will explain how we define Tier Zero and explain what common assets we recommend to be part of Tier Zero."
"Enjoy a quick peek into the beauty of Windows computing. From the MZ for the DOS MZ executable and it’s oft used ?xml eXtensible Markup Language companion files, to the rare XEX2 Xbox 360 executable format utilized in the bootstrapping process for streaming media from Windows Media Center."
"Recently, I had the privilege to write a detailed analysis of CVE-2023-34362, which is series of several vulnerabilities in the MOVEit file transfer application that lead to remote code execution. One of the several vulnerabilities involved an ISAPI module - specifically, the MoveITISAPI.dll ISAPI extension. One of the many vulnerabilities that comprised the MOVEit RCE was a header-injection issue, where the ISAPI application parsed headers differently than the .net application. This point is going to dig into how to analyze and reverse engineer an ISAPI-based service!"