- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-06-08
ITSEC Newsletter 2023-06-08
Red team is best team
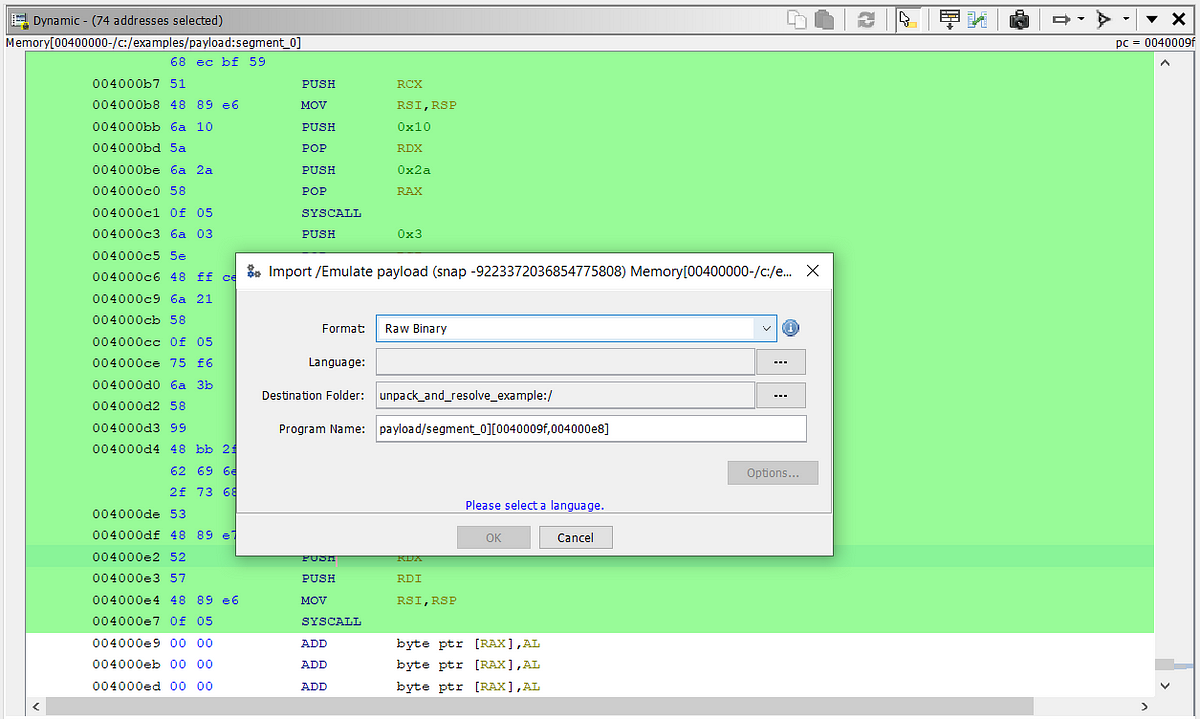
"It is a pretty common practice for malware authors to decode and execute payloads in memory to avoid detection and complicate analysis efforts. In this post, I will decode and start analyzing an XOR encoded Metasploit TCP reverse shell to give an example on how to get started with this using Ghidra to emulate the payload."
"A philosophy that has stuck with me is to only make the minimum changes necessary to circumvent a particular static signature - i.e. solve the problem with a scalpel rather than a sledgehammer. This post will present a methodology for identifying “bad bytes” in a payload and finding their location within the compiled binary. To demonstrate, I will use ThreatCheck and Ghidra to analyze and modify a Beacon payload generated from Cobalt Strike."
"In short, OneDrive can be the best way to do user enumeration because:
*It doesn’t require a login attempt
*It’s completely silent (companies cannot see the requests)
*There’s no rate-limiting"
"I recently released a tool called Debloat. The purpose of Debloat is to remove junk bytes from bloated executables. … If you are unfamiliar: there is a trend where many threat actors add 100 – 900 MB (or even up to 3 GB) of junk bytes to their malware to prevent analysis. This junk, or bloat as I call it, typically makes it difficult for AV engines to scan the binary and the size of the binary also exceeds the maximum capacity of most sandboxes thus preventing automated analysis. For example, many public sandboxes have a limit of 100 MB and VirusTotal has a limit of 700MB."