- ITSEC Newsletter
- Posts
- ITSEC Newsletter 2023-06-01
ITSEC Newsletter 2023-06-01
Red team is best team
"Parent Process ID (PPID) Spoofing is a technique used to aid in hiding malicious code from identification. This technique will falsify the PPID of the current executable to be that of any arbitrary process accessible to the current user. By falsifying this PPID, it would appear to any investigator that the current execution belongs or has been started by another benign process. During Incident Response cases, one (1) of the first tasks is to identify if any executable is having an odd or out of place parent. PPID hinders this by making the executable appear to be started by an acceptable process. An example would be if an executable was started by an Excel.exe file, which would raise suspicions of the investigator and warrant further analysis. However, if the process was started by svchost.exe, it would most likely not be immediately seen as suspicious."
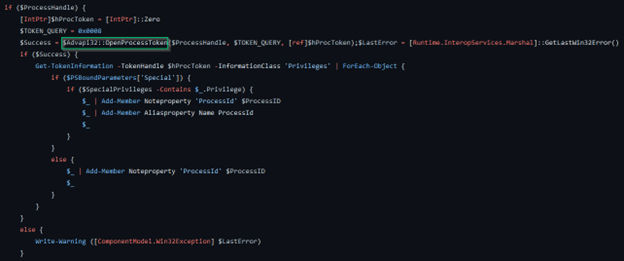
"For this effort, I decided I would use a fairly straightforward tool for my analysis. Within Powersploit’s Privilege Escalation module there is the PowerUp script written by Will Schroder, which includes a function called Get-ProcessTokenPrivilege. This function is not necessarily malicious by itself, but it had what I needed to better understand the methodology for analyzing the function call stack."
"At the end of the last post, we had the ability to read memory out of the target process, but we still had very little in the way of interpreting the data in that process. That changes in this post, where we will start grabbing useful information out of the target, including modules, exports, and even private symbols."